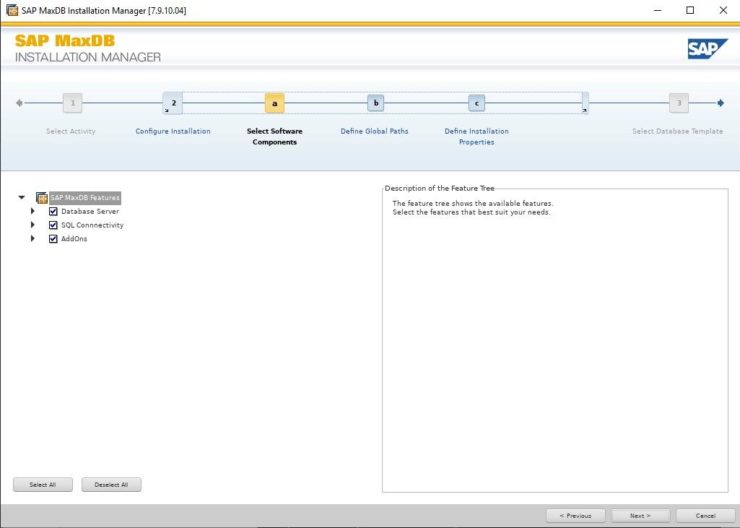
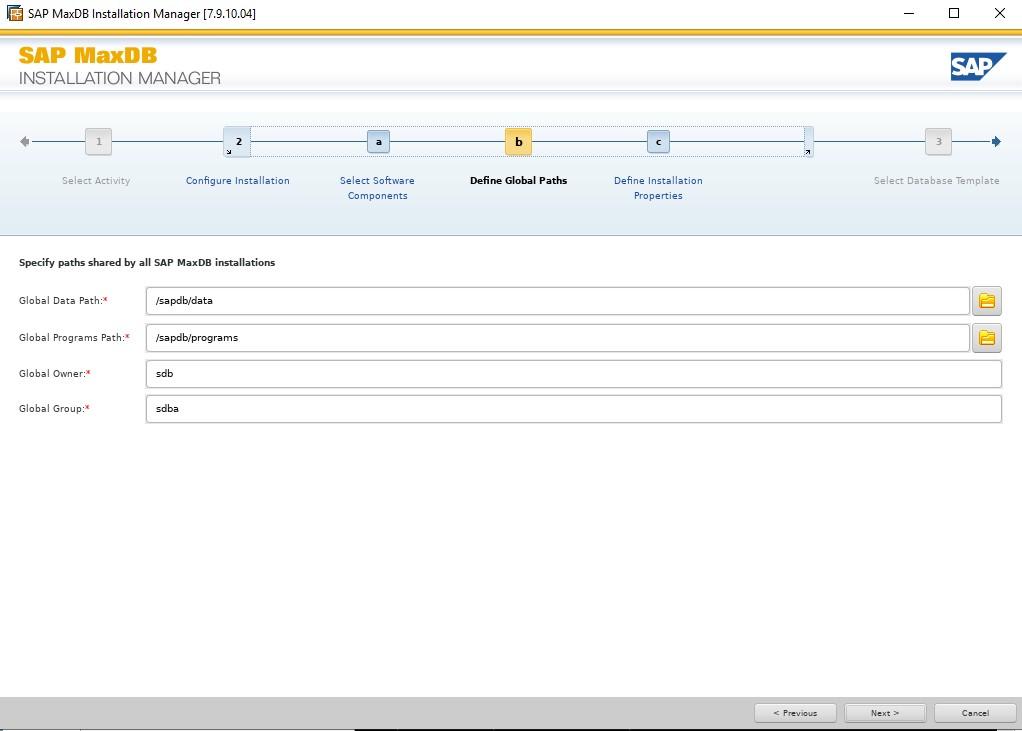
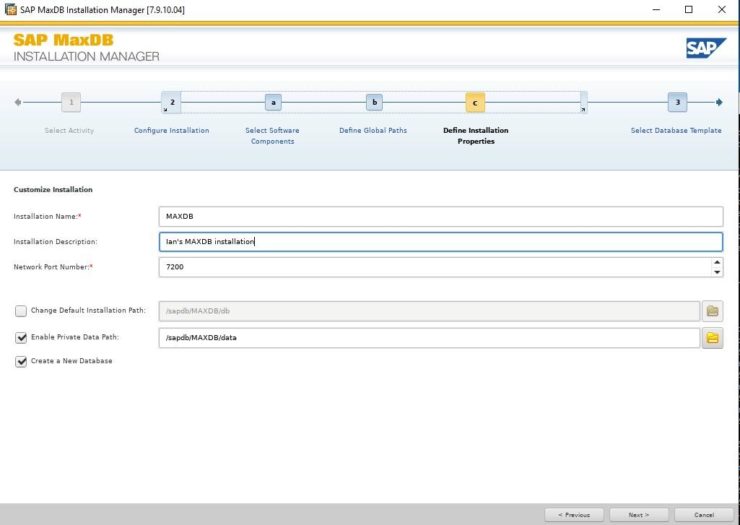
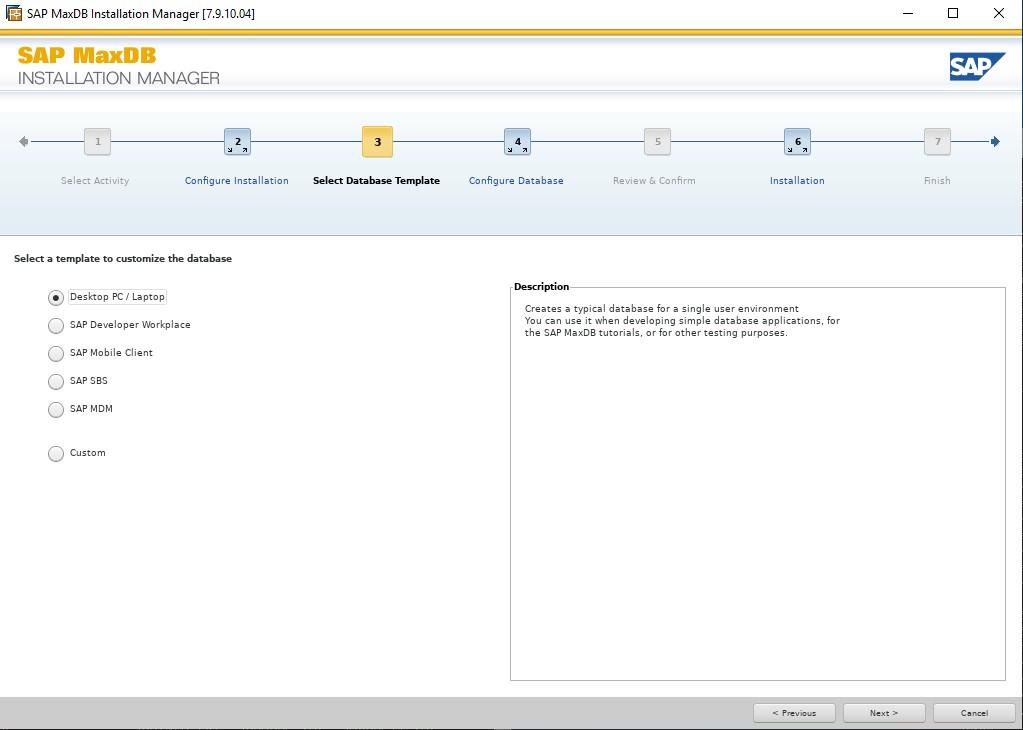
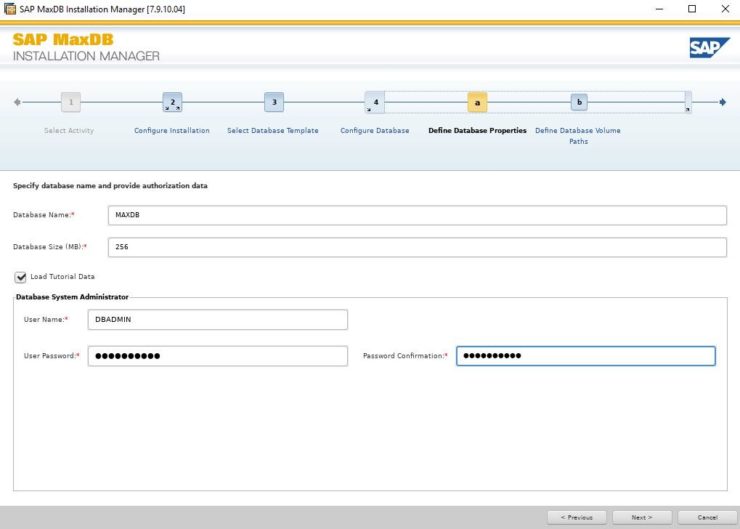
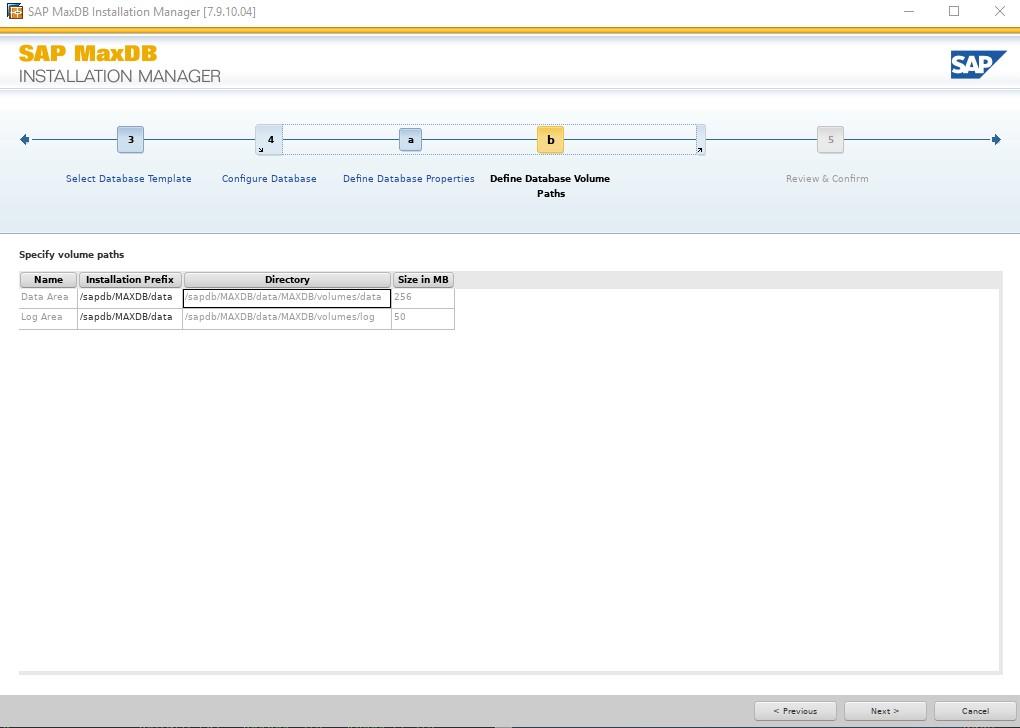
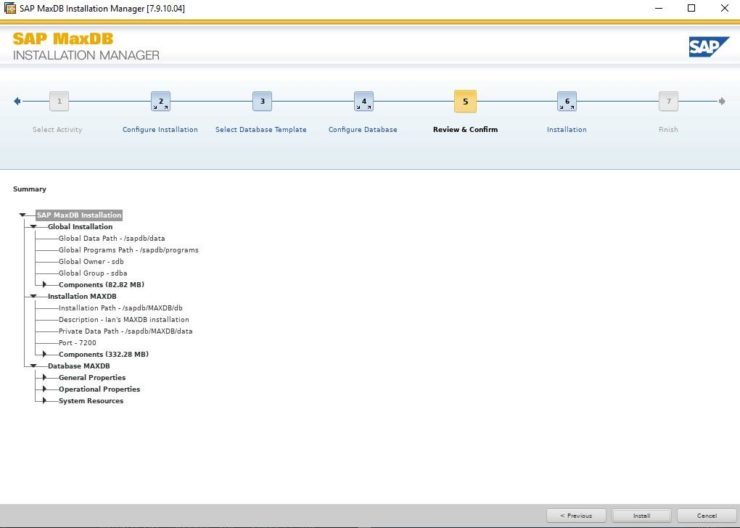
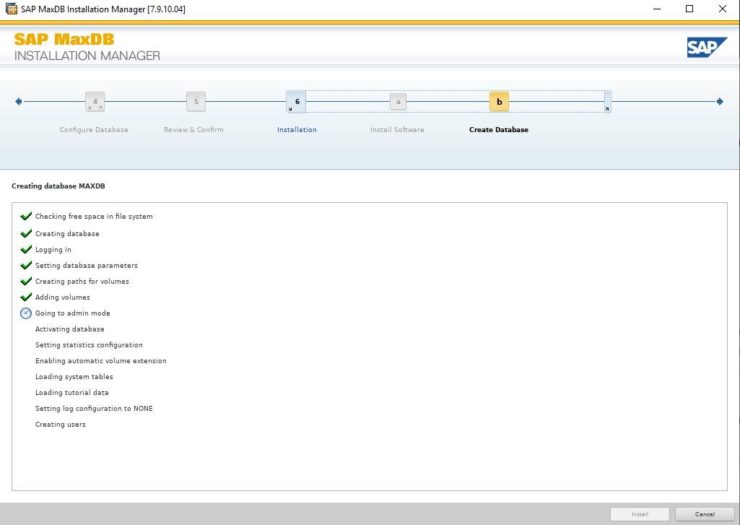
SIOS LifeKeeper for Linux v 9.8.1 improves the way companies manage HA/DR
In today’s tech-driven landscape, companies are seeking innovative solutions to effectively maintain their complex application environments. In this video, Todd Doane, sales engineer at SIOS Technology, explains how the latest version of SIOS LifeKeeper for Linux helps companies in safeguarding critical enterprise systems against downtime and disasters. “The release features a new Web Management Console. It’s self-contained and does not require additional installations or third-party add-ons,” says Doane.